Address Poisoning in Crypto: What It Is, How It Works, and How to Stay Safe on L2 Networks
Learn how address poisoning scams work, why they’re rising on Layer 2 networks, and how to protect your crypto from being sent to the wrong wallet address.
By Obafunso Ridwan, Joseph Samuel, Akin Ebenezer
July 02, 2025

The crypto space is evolving fast. Gas fees are cheaper, transactions are faster, and Layer 2 (L2) solutions are making blockchain more accessible than ever. But with all this innovation comes a new wave of exploits—one of which is quietly stealing funds from unsuspecting users. It’s called address poisoning, and it’s becoming a common threat across major L2 networks like Optimism, Base, Arbitrum, etc.
In this post, we’ll break down exactly what address poisoning is, how it works, and more importantly, how you can protect yourself from falling victim.
What Is Address Poisoning?
Address poisoning is a scam tactic where an attacker creates a wallet address that looks similar to a legitimate one—usually one you’ve recently interacted with. The goal is simple: trick you into copying the wrong address during a future transaction, causing you to unknowingly send your funds to the attacker.
It preys on muscle memory, inattention, and the natural habit of copying and pasting addresses from your recent transaction history or block explorer. Since crypto wallet addresses are just long strings of letters and numbers, it’s easy to miss subtle differences.
How Address Poisoning Works
The scam might seem technical, but it’s surprisingly simple and cheap to execute—especially on L2s where gas fees are low. Here’s a breakdown of how it plays out:
Vanity Address Generation
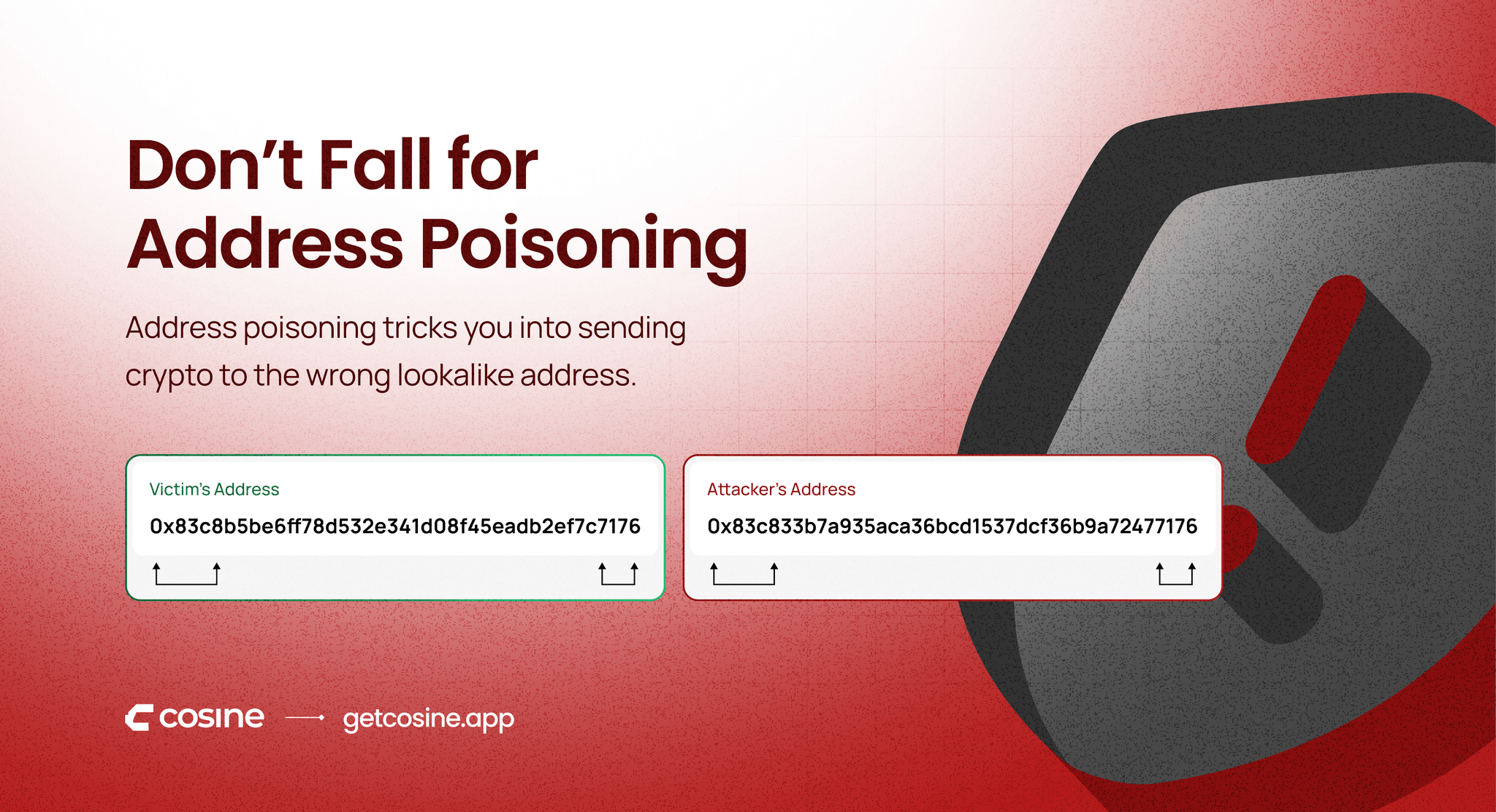
Attackers use automated tools that allow them to create vanity addresses. These are addresses customized to start or end with certain characters. So instead of a completely random string, they might generate something that looks like:
Victim’s address: 0x83c8b5be6ff78d532e341d08f45eadb2ef7c7176
Attacker’s address: 0x83c833b7a935aca36bcd1537dcf36b9a72477176
Only a few characters are the same, and at a glance, it can be hard to notice.
Fake Transactions to Your Wallet
Next, the attacker sends a small or zero-value transaction from the vanity address to your wallet. These can come in different forms:
- Zero-value transfers of real tokens like USDT, USDC, or DAI
- Transfers of fake tokens with identical names to legit ones
- Small real transfers (e.g., $0.001 in native coin or stablecoins)
Because these transactions show up in your wallet’s history, many users copy that address thinking it was part of a legitimate transaction.
You Make a Mistake
Later, when you want to send crypto back to a friend, an exchange, or your other wallet, you scroll through your wallet history or use your explorer and copy the wrong address—the attacker’s poisoned one.
You hit send. The funds are gone. There’s no undo button.
Why It’s More Common on L2
Layer 2 networks like Optimism, Base, and Arbitrum are booming. But their low gas fees make this kind of scam even easier to pull off:
- Attackers can spam hundreds of fake transactions for just a few cents.
- The sheer volume of activity on L2s buries the signal in noise.
- Many wallets still display poisoned transactions without checking their legitimacy.
This has created a fertile ground for attackers to thrive.
How to Prevent Address Poisoning
The good news? This scam only works if you make a mistake. So by staying cautious and building good habits, you can completely avoid it.
What NOT To Do
- Never copy wallet addresses from your transaction history. This is exactly where attackers plant the trap.
- Don’t trust addresses shown on block explorers without verifying. Block explorers show vanity addresses just like any other.
- Avoid interacting with any strange or unexpected transaction in your history—especially those involving small or zero-value token transfers.
What TO Do Instead
- Always copy addresses from your wallet’s receive screen. This ensures you're getting the correct destination address.
- Double-check before every transfer. Even if you recognize the address, take a moment to verify it.
- Send a small test transaction first—especially when sending large amounts. Confirm the funds arrived before sending the rest.
- Use human-readable addresses like Ethereum Name Service (ENS) or Cluster Domains. Instead of 0x83c8...7176, you can send to yourname.eth or cluster/main.
- Choose wallets with built-in protections. Some wallets, like Cosine Wallet, hide poisoned transactions from your history to help protect you from address poisoning scams.
Wallets That Offer Protection
Some modern wallets are stepping up to fight address poisoning. They’re using AI heuristics, flagging zero-value transfers, and providing cleaner, filtered transaction histories.
Look for wallets with:
- Security alerts
- Hidden spam transfers
- ENS or Cluster domain support
Even then, you are the last line of defense. Stay alert.
Final Thoughts
Address poisoning isn’t the most sophisticated scam in crypto—but it’s alarmingly effective. It doesn’t rely on exploiting bugs in smart contracts. It relies on you making a small mistake, and once the crypto is sent, it’s gone forever.
As we move toward mass adoption—especially on L2s where users are newer and fees are cheaper—education is the strongest shield.
Share this with your friends, your family, and your Telegram group. Next time you send crypto, slow down for 5 seconds and double-check. That could save you thousands.
Stay sharp. Stay safe. 🛡️
TL;DR
- Address poisoning tricks users into sending crypto to wrong (but similar-looking) addresses.
- It works by injecting fake or small-value transactions into your history.
- It’s spreading fast on L2s due to cheap gas fees.
- Always copy addresses from your receive screen and use test transactions.
- Avoid copying addresses from history or block explorers.
- Use human-readable names like ENS or Cluster domains.
Share Article
Related Article
Defi
HD Wallets: The Smarter Way to Manage Multiple Wallets with One Backup
July 20, 2025
Obafunso Ridwan, +2

Defi
Why Self-Custody is the Future of Crypto: Taking Control in a Trustless World
May 12, 2025
Obafunso Ridwan, +2